404
The first privacy tool built for a world where the server is the primary surveillance actor.VPNs hide your IP. 404 hides you.
What does 404 not do?
404 is not a VPN or ad-blocker.Traditional privacy tools disguise your location or block ad-domains/scripts. 404 disguises your identity at the behavioral, TLS, and system-telemetry layers.
404 is experimental software!
| Fingerprint | VPN | 404 |
|---|---|---|
| Location | Yes | / |
| Browser | / | Yes |
| OS | / | Yes |
| JavaScript | / | Yes |
| Hardware | / | Yes |
| TLS cipher-suite | / | Yes |
| TCP/IP options | / | Yes |
Why does 404 exist?
Surveillance has evolved beyond the scope of ad-blockers and VPNs. Websites now identify you using:- Browser/OS combinations
- JavaScript values
- TLS cipher-suites
and more...
You produce dozens of semi-unique values across the internet ranging from your browser to how your specific GPU renders a single pixel. This data is passively collected by companies anytime you interact with their servers.These vectors allow servers to identify users confidently across multiple sessions over the span of months or even years.404 exists to give users meaningful control over their data in an environment where surveillance is no longer optional or avoidable.
What does 404's proxy layer do?
404's STATIC proxy is a Rust-native TLS middleware that rewrites client fingerprint signals at the handshake and application layer, 100% locally.It creates a coherent identity that matches real browser behavior, allowing users to browse with a believable and session-stable fingerprint.
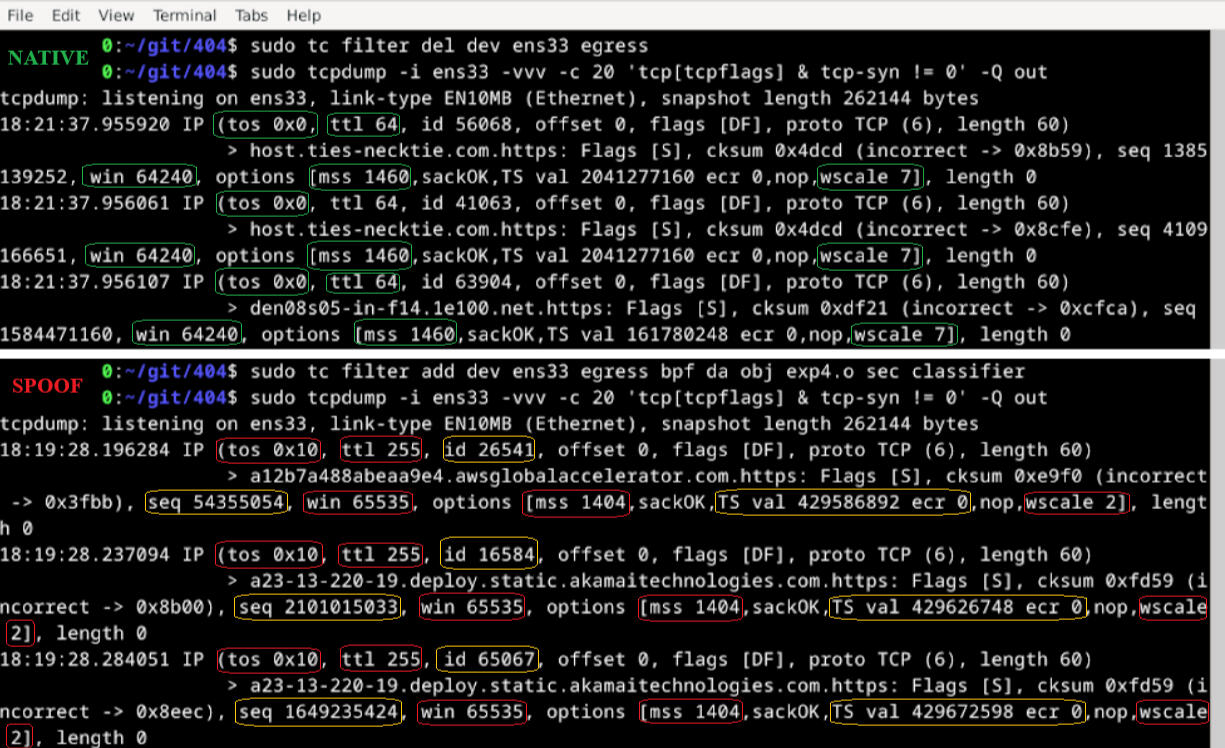
What does 404's eBPF layer do?
404's eBPF layer allows users to modify network packet values such as TTL, MSS, window size/scale, and more, to match the same profile that STATIC is spoofing.As client fingerprinting advances and users become more and more unique, we need to be more deliberate about the data that we provide to the server.Currently, different OSes implement their TCP/IP stacks differently, exposing a fingerprint. Tools like nmap and p0f utilize these passively connected network telemetry values and can semi-precisely identify un-hardened network stacks just by observing packet header values and behavior.
404 - Not Found (on purpose)
If you want to learn more, or want to just chat, you can contact us via email or join the Discord server below.
404 is a small, experimental research project. The software and materials here are intended for research and defensive use only. By default, no data is transmitted off your machine; if you choose to enable external data flows you do so at your own configuration and risk.We do not provide documentation or support for exporting user data. The code is provided as-is; while it was authored and tested by the project team, no security or operational guarantees are made. Use responsibly and on consenting or disposable systems.Copyright 2025. GNU GPLv3.